

DESTROY xdph users with this one simple trick!
Published 2024-09-28 (UTC)
Hey all.
I’ve been wasting a ton of time on Satisfactory ever since 1.0 released and kind of doing absolutely nothing else. I should really write some code again.
As of writing, I’m on Tier 6, and in the middle of building a railway. I was, however, feeling reaaallly lonely, so I tried streaming to friends (who didn’t own Satisfactory nor even care to see me play), and… Vesktop just crashed.
Of course, my brain immediately shot to either my system or Vesktop being out of date. On my desktop, I use the Vesktop flatpak, so
I performed both a full system update and ran flatpak update.
Turns out Vesktop wasn’t out of date. Whatever. Probably fixed now. So I tried again, and… Vesktop still crashed as soon as I dared click the screenshare button.
Cool! Alright. Time to mull over logs.
Vesktop was complaining about not receiving a screen before crashing, and strace showed nothing, so I checked out journalctl, and saw…
xdg-desktop-portal-hyprland[22647]: sh: -c: line 1: syntax error near unexpected token `('…an sh syntax error under xdg-desktop-portal-hyprland?
Weird. I read the triggering line, and figured that it was probably some Firefox window, so I closed the tabs of any Firefox window I had open with parentheses in the title, and got a different error:
xdg-desktop-portal-hyprland[23523]: sh: line 1: More: command not foundxdg-desktop-portal-hyprland[23525]: sh: line 1: Cloudflare: command not foundxdg-desktop-portal-hyprland[23524]: sh: line 1: Minecraft: command not foundxdg-desktop-portal-hyprland[23522]: sh: line 1: does: command not foundxdg-desktop-portal-hyprland[23526]: sh: line 1: coolviruses.download: command not foundOh. Huh. Those are just… random select words from my browser’s tabs.
Okay, so surely it wouldn’t work if I just… closed Firefox, right?
…right?
…Nope. It worked without Firefox. I read the line triggering the syntax error again, and then decided to try something…
Oh! Okay! That… shouldn’t happen!
At this point, I was still confused. I had assumed it was a Vesktop vulnerability, but I wasn’t so sure. So I quickly decided to ask Jack, who uses GNOME, if he could reproduce the issue.
And he couldn’t. Now we were even more confused. I was… kind of tired and lazy, so I got him to create a proper proof of concept to see whether it was was Vesktop or xdph.
Okay, so it’s xdph. Cool!
At this point, I realized that we should probably report this, so I switched out mpv for a notification:
…and Jack disclosed the vulnerability to Vaxry.
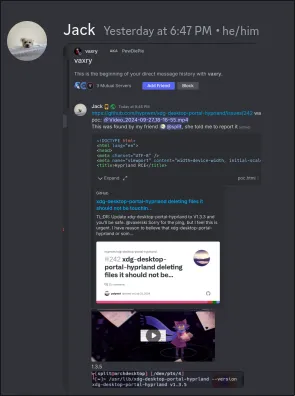
Anyway: 6 hours before the writing of this post, xdph v1.3.6 was released.
v1.3.6 contained commit dcfabff, which fixed this vulnerability. I obviously heavily recommend that you update.
This vulnerability occured because xdph’s code only properly filtered all characters after the first. The first character in a window’s title is still filtered, but the code incorrectly filtered out double quotes instead of single quotes.
To cap this post off, here’s a demonstration:
if you're using xdph 1.3.5 and below,

By the way, this demo uses mpv and its yt-dlp integration. Make sure to install both.
If you don’t have JavaScript enabled, you should be able to keep this window open to this tab and screenshare almost anywhere else to trigger the demo 🙃
In Chromium, you’ll need to click on either the Window or Screen tab for it to make a request to the portal and trigger the bug.
Extension to this post: In xdph 1.3.2 and below, the problematic environment variable used double quotes instead of single quotes, which requires you to run commands using string interpolation instead of by ending the string. The title has been updated to accomodate for 1.3.2 and below.
Thanks to Jack for helping me write this post.